BUGKU_CTF杂项题之1和0的故事
01文本非白即黑锁定二维码考点:
python脚本:
from PIL import Image
MAX = 25
#二维码大小
pic = Image.new(“RGB”,(MAX, MAX))
str = “”
str为获取的01片段,注意要把01连成一串,因为换行符也是占一位的,会干扰图像
i=0
for y in range (0,MAX):
for x in range (0,MAX):
if(str[i] == ‘1’):
pic.putpixel([x,y],(0, 0, 0))
else:
pic.putpixel([x,y],(255,255,255))
i = i+1
pic.show()
pic.save(“1.png”)
#由于直接预览分辨率太低,所以保存下来观看
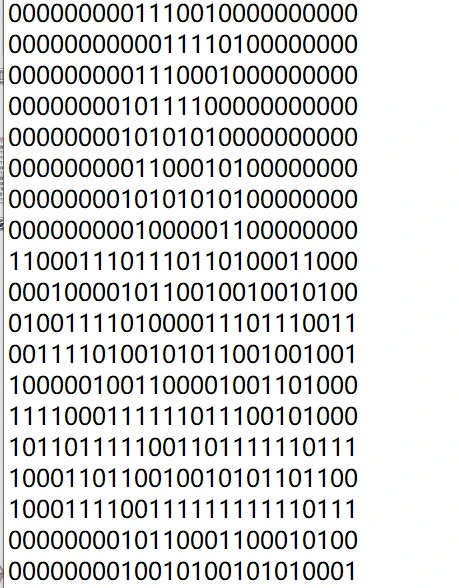
得出的残缺二位码

缺少定位符

用windows自带的3D画图插入补全定位符即可
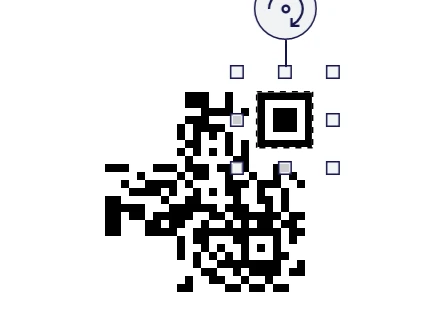
因为很难对齐定位符,所以直接根据3D中定位符的最清晰长宽像素比来修改01字符串即可,我这里最清晰的是7像素,
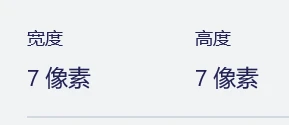
所以在01字符串上修改出对应的01位再运行脚本即可(1是黑,0是白,保持对称,中间留3,注意!!!残缺的三边都要修改!!!)
 没修改前的一连串01:
没修改前的一连串01:
0000000001110010000000000000000000001111010000000000000000011100010000000000000000010111100000000000000000001010101000000000000000000011000101000000000000000010101010100000000000000000100000110000000011000111011101101000110000001000010110010010010100010011110100001110111001100111101001010110010010011000001001100001001101000111100011111101110010100010110111110011011111101111000110110010010101101100100011110011111111111011100000000101100011000101000000000010010100101010001000000001010101010001100100000000001001111111100100000000000011001011110111000000000100110010010000100000000110000110110110010000000011010000101110101
修改后的01字符串:
忘记写了,自己搞吧
